How to setup passwordless SSH login in Linux.
This brief tutorial is going to show you How to setup passwordless SSH login in Linux. The reason you may want to do this is to enable more secured form of authenticating to your SSH enabled servers.
As a system administrator, you plan on using OpenSSH for Linux and automate your daily tasks such as transferring files or database dump file for the backup to another server. To achieve this goal, you need to log in automatically from the Server A to Server B. Login automatically mean you do not want to enter any password because you want to use ssh from a shell script.
SSH (Secure SHELL) is an open source and most trusted network protocol that is used to login into remote servers for execution of commands and programs.
It is a client and server protocol, and it helps us to access the remote system over the network through the encrypted tunnel. Whenever the client access the server, the client downloads the secure key from the server and at the same time-server also downloads the key from a client. Those two keys make the encrypted tunnel between the server and client, so that data transfer very securely over the network.
This tutorial will cover How to setup passwordless SSH login in Linux.
Setup Passwordless SSH Login on Linux.
This steps tested on CentOS 5/6/7, RHEL 5/6/7 and Oracle Linux 6/7.
Node1 : 192.168.0.114 (linux3)
Node2 : 192.168.0.115 (linux4)
Generate authentication key
If an SSH authentication-key file does not exist, generate one by running the ssh-keygen command. When prompted for a passphrase, use a blank passphrase if fully password-less login is required:
ssh-keygen is a Unix utility that is used to generate, create, manage the public and private keys for ssh authentication. ssh-keygen creates RSA keys for SSH protocol version 1 and RSA or DSA keys for use by SSH protocol version 2.
# ssh-keygen -t rsa
Upload Generated Public Keys to – node2 :
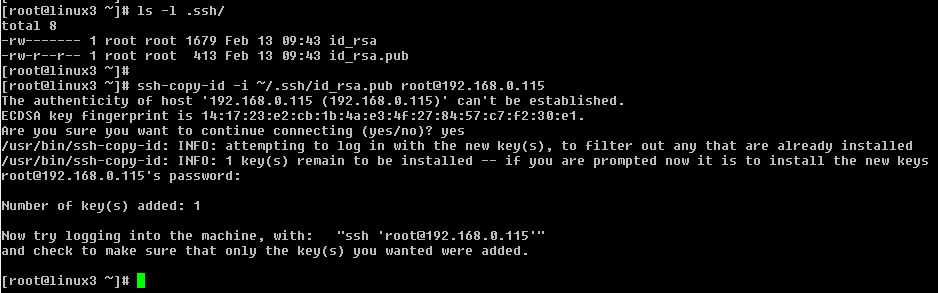
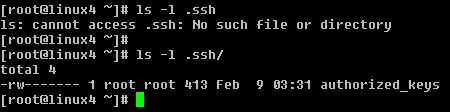
Use the ssh-copy-id command to install the public half of the newly-generated authentication key into a specific user’s home directory on the remote host. The ssh-copy-id command will then automatically append the identity information into the ~/.ssh/authorized_keys file for the specified user on the remote host (creating ~/.ssh and~/.ssh/authorized_keys if necessary).
# ssh-copy-id -i ~/.ssh/id_rsa.pub root@192.168.0.115
Node2 : 192.168.0.115 (linux4)
Alternatively if the server is not installed with openssh-clients (a package which provides ssh-copy-id command utility) you can copy the authentication key with the command:
# cat ~/.ssh/id_rsa.pub | ssh user@remote-host "cat >> ~/.ssh/authorized_keys"
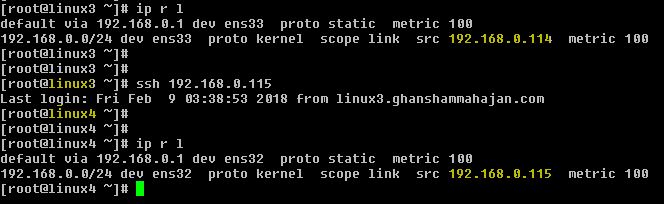
If everything is configured right, now access the remote machine using SSH. It will take you to the shell directly without asking password.
# ssh 192.168.0.115
Thanks for reading the post 🙂 . Please share and leave your comment if any.


Pingback: buy ciprofloxacin
Pingback: albuterol inhaler
Pingback: generic viagra pills for sale
Pingback: naltrexone for weight loss
Pingback: buy generic 100mg viagra online
Pingback: acetaminophen
Pingback: cheap cialis online without prescription
Pingback: chloroquine price in india
Pingback: hydroxychloroquine order
Pingback: buy cheap viagra without prescription
Pingback: buy cialis
Pingback: cheap geneirc viagra 100
Pingback: bimatoprost for eyelash growth